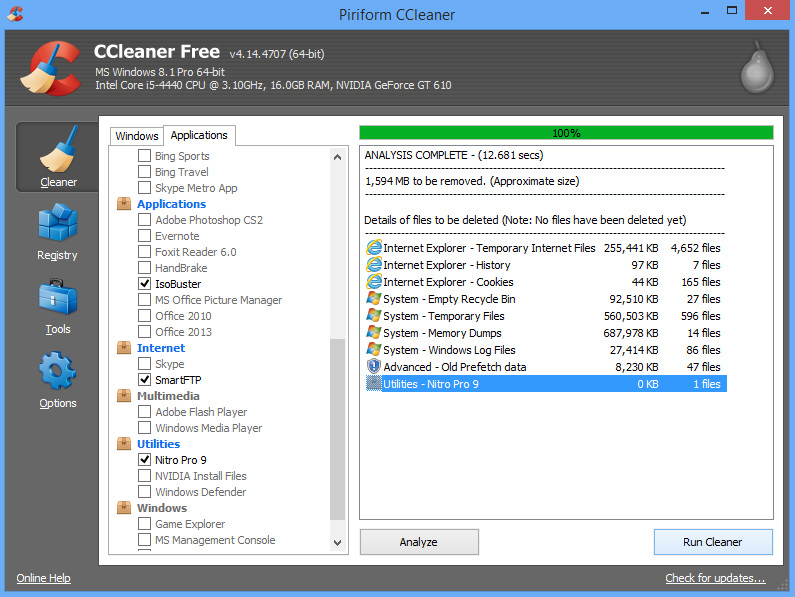
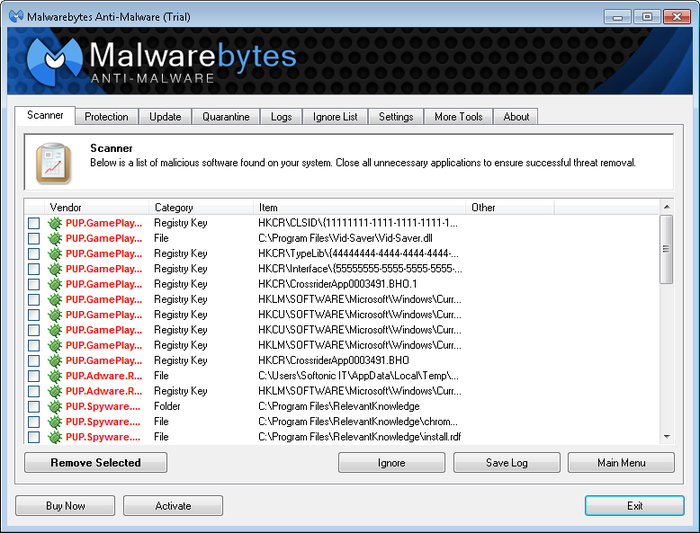
 It's been a while hasn't it? Well there's a good reason for that: we've been working on a big web project which will be released by the end of this year (hopefully) so stay tuned! Anyway, today's topic is how to clean up the junk files that remain on your computer after installing programs, accidently agreeing to install adware, etc. These files can be irritating, take up free disk space, and slow your PC down when they accumulate. Furthermore, some of these junk files are actually executables and run silently in the background; making them likely culprits for unusual lags and slow performance. So to clean junk files, there are two main tools that we use: CCleaner and Malwarebytes. Both are completely free and very effective at getting rid of junk programs and the debris they leave behind. CCleaner As the name suggests, CCleaner, is a program that cleans your PC of unnecessary files. However, most people don't know what the 'C' stands for; looking up CCleaner on Wikipedia might give you a bit of a chuckle. Anyway, CCleaner has been 'cleaning' computers for over 12 years, so it's reliability can't really be questioned. However what about its effectiveness? Well we've placed CCleaner to the test, on a computer that was filled with adware and a lot of junk data. What happened? Take a look below! As you can see, CCleaner can help you a lot with removing unnecessary files; freeing us 1.5GB of disk space: a space saver for those who use SSDs! However, although CCleaner removed most of the unnecessary files from the PC, it did not remove any of the adware and junk programs that were running in the background. To amend this issue, we turn to our second tool: Malwarebytes Anti-Malware. Malwarebytes Anti-Malware  Malwarebytes Anti-Malware is one of the programs that we are a big fan of because: 1. It is free 2. It works well 3. It was originally written in Visual Basic 6, which is one of our favorite IDEs/Languages until Lazarus came along! But how well does it work? To find out the answer to that question, we placed it to the test on our very own adware/junk filled PC. Not surprisingly, the results were very respectable. As you can see, Malwarebytes picked up a lot of unwanted programs, adware and even spyware that CCleaner missed. This is mainly because MBAM, is an anti-malware/anti-spyware program, while CCleaner is a general purpose junk cleaning application. If we only used MBAM to clean junk files, it will miss all the temporarily files that CCleaner helped us clean.
Therefore, in this way, if you want to clean up junk programs and files on your computer, make sure to use both these tools to get the best from both worlds: CCleaner to free up disk space, and Malwarebytes to remove those nasty junk programs that run on your PC!  So you finally decided to just jump in to it. You are going to make an app on Windows. But there's just one problem: you don't know much about programming or even computers. What should you do? Being a software developer myself, I can still recall how I got in to developing software. At first, I was just really bored. So I spent my time playing around with windows, creating folders, shortcuts, etc; until I got bored of that. That was when I decided to just jump in and learn how to code. When starting to learn code, the best way to keep yourself interested and motivated is to start with something that's easy and simple. I personally recommend downloading Visual Basic and playing around with it. Start off by just adding buttons and texts to your program's window and personalising it with things you like. For example, I created my own bank account management system, with just two buttons for withdrawing and depositing cash. Soon after you've mastered these baby steps, move on to more advanced endeavours. For me, it was creating a program that scrambled any text I typed in and unscramble any scrambled text that was fed back. I also developed a calculator. After a few months of messing around with VB and making the apps that you have interest in developing you will begin to develop a strong sense of familiarity and excitement with coding. Give it another few months or so and you will begin to envision all sorts of programs to develop; virtually anything you can imagine. After mastering the basics of Visual Basic, try to learn more versatile languages such as C, C++, Java or C#. So what are you waiting for? Get started now by downloading the latest version of Microsoft Visual Studio and get started. Remember success is not a destination: it's a journey.
This article will not talk about what should you do. Instead, we focus on what should you have done. If you are looking for advice, we have previously published articles on how to recover your deleted files, recover files from deleted partitions and even recover files from a computer that does not boot.
What you should have done is backed up your files. Backup is one of those things that are so underestimated and overlooked, that when you actually need it, its not there. So how do you ensure the safety of our data before it accidentally gets deleted, or crashes? We back them up. The best utility to use for backup in our opinion is the one that is provided with with Windows: Windows Backup. Why do we recommend using this? Because its free, and it works. Windows Backup saves your entire hard drive to a single file, which should be stored in an external hard drive. An external hard drive is basically a massive USB that is used to store files from 500GB to 3TB. So if your hard drive has 1TB of space, buy an external hard drive of at least 1.5TB, as some of the space may be used by the drive's internal software. So now you have bought your 2TB external hard drive from the store, and you want to backup your current hard disk. How do you do it? Follow the step by step guide at our friends Microsoft. This method is the best as it copies everything so incase the whole hard drive goes missing, or corrupts, your data can be easily accessed on the external hard drive you bought, even the little files that you didn't think mattered. We recommend you back up your whole hard drive once at month because at this rate, any significant changes/new files you have made will be safe, stored and ready to restore when your computer decides to stop working. However, because of an emerging technology that has caught our eye, our article does not stop here. This thing that has scored its place in our prestigious article is called cloud storage. Cloud storage is the storing of your files on the internet, so it can be accessed from anywhere, anytime. This means that you can upload your entire essay collection on Google Drive, turn off your computer, but still be able to access and modify them at somewhere far away, ie, school. How does this relate to backup? The connection is obvious. Your files can be stored on the most reliable cloud storage provider, Google. In case your computer gets stolen, or you accidentally break it, your files will be sitting soundly online. Furthermore, Google Drive places the cherry on top of the cake by allocating a folder on your computer called 'Google Drive'. This folder will be synced with your files on the cloud, and any changes to the files in the folder will also be made to those on the cloud. Hence, by using Google Drive to store your important data, you essentially possess an invisible USB stick that you can plugin by simply logging on to Google Drive. That's all folks. Stay safe and back up your data. XetoWare
We can't track an ordinary link. For example, the link to our popular extracting software is 'http://www.xetoware.com/uzip.html'. But if you shared this link, there is no way you can see how many times users have clicked it, where they are from and what operating system they.
So how do you solve this problem? You use an url masking service. What is it? An url masking service or url shortener is an online service that lets you convert your link to another link, often to shorten it. However some url masking services such as Bitly offer click analytics, which allows you to see intricate details such as how many times this link has been clicked, which countries have clicked it the most, etc. Bitly is great! It has been around a long time, and is therefore, very reliable. But how do we use Bitly? To see detailed analytics of your clicks such as geographical and operating system data, you will need to sign up to Bitly. Simply head over to their website, and the rest of the process should be very intuitive. After you have made your account, copy the link you want to track, and shorten it using Bitly. Now your link should look something like this: http://bit.ly/1Ovja9k. Now by sharing this link with your users/friends, you can begin to track your clicks. How? By simply adding a '+' character after the Bitly url. For example, if I wanted to track the clicks on the link bit.ly/1Ovja9k, I will simply add a '+' at the end and then open that link in my web browser. So I can see how many clicks I got, which countries my users reside in, etc by going to this link: http://bit.ly/1Ovja9k+. So we come to the end of another informative article. If you think you've learnt something useful from this article, please don't hesitate to share it! Peace.
Well the most common method of hacking a naive victim is to convince them to run a virus. Why would they even do that, you may ask, well its simple, they don't know its a virus! These days, viruses come with toolkits that help the evil hackers create them with ease. A simple Google search will reveal the toolkits available that can engineer a virus within seconds. Once the hackers make their virus, they upload it to file sharing websites, blogs, download websites, etc disguised as a legitimate program. Some smarter hackers even bundle their viruses with legitimate programs and trick the user in to believing that they have run the real deal. An example of this can be the setup of a free video converter bundled with a virus that can control your computer, steal your information, etc. Once downloaded, and the single program is run, two programs, the legitimate video converter setup is run, as well as the virus, hence, tricking the user in to believing that they have just opened a safe file.
More advanced techniques of hacking involve leveraging the power of Java. Advanced hackers will often make a Java applet that appears legitimate, but when run, downloads the real virus and executes it. This way the user thinks that they have ran a harmless Java web program, but in reality, the web applet has downloaded a harmful Windows EXE to their computer and opened it! Sounds scary right? Well luckily, XetoWare will discuss how to avoid getting hacked below. When it comes to avoid getting hacked, the first thing that comes to mind is an antivirus program: and we definitely agree. Most users are looking for something free, and so are we. The best free antivirus program currently out there, in our opinion, is AVG. AVG will protect you from about 98% of threats, and is also decently resource effective. An antivirus is required because it not only scans every runnable file before you even open them, but every file at the second they are created! In this way, any threats are scanned and eliminated before you can open even touch them, protecting you from general as well as advanced methods of hacking. But antivirus are just one part of the journey to full protection against hacking. Some hackers will even try to infiltrate your network, attempt to use buffer overflow attacks to inject code in your unaware system. What can you do then? Get a firewall is our answer to that. A firewall readily blocks insecure connections, as well as those that are blacklisted or have a bad reputation. Fortunately, Windows already provides a pretty decent firewall, called, you've guessed it, Windows Firewall. However if you are still in great concern, we suggest purchasing AVG Internet Security for full protection. On the other hand, if you are looking for something cost effective, Avast offers a pretty decent free firewall and internet protection package. Lastly, use common sense. With common sense, you can already filter out 80% of the threats online. That is: Do not go to suspicious, unpopular websites, especially those offering free downloads Do not download unpopular, illegal or suspicious files Do not run Java applets from unpopular websites Do not run anything unless you have downloaded it from a reputable source such as CNET, Softpedia or Microsoft But how do you really know if a program is safe? There must be an easy way right? Yes there is. If you must know if an unpopular file is safe to run or not, upload it to VirusTotal, but make sure unpack it first, if you have downloaded it as a ZIP or RAR. Well, that's it! By reading this article, you have obtained valuable information on how to shield yourself from the great threats of the internet! Stay safe! XetoWare
1. Download WinRAR
However WinRAR is not free, and will continually nag you to 'register' it. Besides that, you will also receive a lot of functions that general computer users do not need. However, if you prefer installing a comprehensive and extensive shareware to extract your RAR, ZIP or 7z archives, WinRAR is the way to go. You can download WinRAR from here. 2. Download WINZIP WinZip is similar to WinRAR in a lot of ways, however, once again, it is not free. As you can expect, nag screens, reminders and other sorts of ways to get you to purchase the full version will occasionally come up. But WinZip is an extensive program, that does the basic needs of extracting ZIP, RAR and 7z files, but also integrates extensively in to your context menu even when you right click on files that are not extractable. 3. Get uZip XetoWare has simplified the extraction process in to a simple, but powerful freeware called uZip. uZip unzips not only RAR, ZIP and 7z, but also less common archives such as gzip, tar, and ISO. On top of that, uZip does not nag you or interfere with your system's context menu: it really is a lightweight utility designed for those who just want the files inside the RAR, ZIP or 7z archives! Download uZip here. So there you have it. Three ways to extract these different types of archives. We personally recommend you to use uZip if you just want to extract the files and move on with your work. However, WinZip and WinRar come in useful when you want to perform extensive actions such as Zip and email files, repair archives, etc. It is just a decision on if you want to purchase their full version after the trial periods expire.
That was ages ago, by the way. I think we chose XetoWare.net.tc. Sounds a bit unprofessional, but hey, we got a website up and running.
However as time progressed, we had to move to a more professional domain name, this website! Feels like home doesn't it? Nevertheless, if you just want to start a free website, the place to go get a short domain name is Smartdots or DotTk, however, if you want a real domain name you should really invest some money, about five bucks, and go buy one from our favourite domain selling company: 1and1 Internet. 
Gmail emails often have dots separating words, such as first and last name. For example, [email protected]. However did you know that the dots really do nothing?
The dots in the email address might as well not be there. Did you know that emailing [email protected] will do the exact the same thing as emailing [email protected]. So the next time you want to sign up to the same website twice, you do not need to create another email account. Just add or remove some dots from your current email address. For example, sending an email to [email protected] is equivalent to blasting one to [email protected] or [email protected]. You can literally sign up to the same website four times with just one email! How great is that! This is called email cheating (XetoWare, 2014). Share this short article if you like it! Here is the code to recursively sort an unique array of integers in Java. public static int[] recursiveSelectionSort(int[] list, int n) { if (n == list.length - 1) { return list; } int temp, lowestIndex = n; for (int i = n + 1; i < list.length; i++) { if (list[i] < list[lowestIndex]) { lowestIndex = i; } } temp = list[n]; list[n] = list[lowestIndex]; list[lowestIndex] = temp; return recursiveSelectionSort(list, n+1); } To test this method, use the code below.
public static void main() { int[] arr = {-1, 10, -999, 20, 1, 2, 3, -100, 200, 20000, 99999, -99999}; System.out.println(Arrays.toString(recursiveSelectionSort(arr, 0))); } Note: Imports java.util.Arrays; is needed at the top of the class file. Happy coding. |






 RSS Feed
RSS Feed